HTTPS Security and Spoofing - Man in the Middle Attack
HTTP stands for Hyper Text Transfer Protocol and is used widely on the Internet. It was okay during the initial years of the Internet for this protocol to ask login credentials etc. as at that place was not much danger of people sniffing your information packets to steal your login credentials for dissimilar websites. When people sensed the danger, HTTPS (HTTP Secure) was invented, which, encrypts the data substitution betwixt you (the client) and the website you are interacting with.
Read: Difference betwixt HTTP and HTTPS.
Until a few years ago, HTTPS was considered foolproof, until a person named Moxie proved information technology wrong by spoofing HTTPS. This was washed using the interception of information packets in the center of advice by someone who spoofed the HTTPS security key to make you believe the connectedness is nevertheless encrypted. This commodity studies HTTPS spoofing where even well-known companies had employed the technique to sentinel you lot and to snoop on your activities. Before understanding Man in the Middle attack, y'all'll need to know about the HTTPS certificate fundamental, which is spoofed to brand you believe nil is wrong.
What Is HTTPS Website Certificate Key
There are certain Certificate Authorities that offer "fettle" certificates to websites. At that place are many factors to determine the "fitness" cistron: encrypted connection, virus-free downloads, and few other things. HTTPS means your information is secure when transacting. Mainly, the HTTPS is used past due east-commerce stores and sites that have data/information that is private for you – such as email sites. Social networking sites similar Facebook and Twitter too apply the HTTPS.
With each certificate, at that place is a key that is unique to that website. Y'all can view the certificate key of a website by right-clicking on its webpage and selecting PAGE INFO. Based on the browser, you will get unlike types of dialog boxes. Look for CERTIFICATE and so THUMBPRINT or FINGERPRINT. That will be the website certificate's unique fundamental.
HTTPS Security and Spoofing
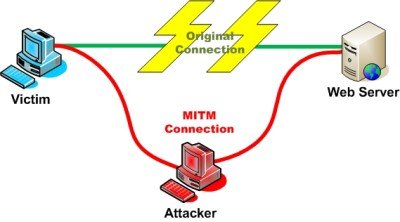
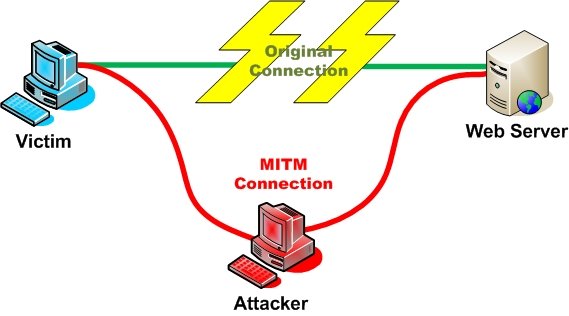
Coming dorsum to how safe you are with HTTPS, the document key can be spoofed by third parties in the middle of clients and websites. This technique of prying upon your conversations is called Human being in the Middle.
Here is how your browser is sent to HTTPS: Either you click on login button/link or you type in the URL.
In the kickoff case, y'all are sent directly to the HTTPS page. In the second instance, where you type in the URL unless y'all blazon in HTTPS, the DNS volition resolve to a folio that directs you to the HTTPS folio using automobile-redirect (302).
The Man in the Middle has sure methods to catch your starting time request to access the website, even if you typed HTTPS. The Human in the Middle could be your browser itself. Opera Mini and BlackBerry browsers do it to catch the communication from the beginning and decrypt it so that they can be compressed for faster browsing. This technique is incorrect – in my opinion – as information technology facilitates eavesdropping but so, the companies say nada is logged.
When you lot blazon in an URL, click a link or bookmark, you ask the browser to make a connexion (preferably) with the secure version of the website. The Man in the Middle creates a simulated certificate that is hard to be identified every bit faulty every bit website certificates have the same format irrespective of the Certificate Issuing Authority.
The Man in Middle successfully spoofs a document and creates a THUMBPRINT that is checked against the "Document Authorities that your browser already trusts". That is, it appears that the certificate was issued by a company that is added to the list of your browsers' trusted document authorities. This makes it believe the document key is valid and provides encryption data to the Man in the Middle. Thus, the Homo in Center now has the cardinal to decrypt the data yous are sending over that connection. Note that Man in the Middle is also working on the other side by sending your info to the website – sincerely but in a way that it tin can read it.
This explains Website HTTPS spoofing and how it works. It also indicates that HTTPS is not fully secure. There are a few tools that would let us know that there is a Human being in the Middle unless one is a highly trained reckoner expert. For the common human, the GRC website offers a method to remember THUMBPRINT. You can bank check out the certificate THUMBPRINT at GRC then match information technology with the one yous retrieved using PAGE INFO. If they match, it is okay. If they do not, in that location is a Human in the Centre.
Source: https://www.thewindowsclub.com/https-security-spoofing-man-in-the-middle
Posted by: piketheirey.blogspot.com


0 Response to "HTTPS Security and Spoofing - Man in the Middle Attack"
Post a Comment